Among other things, 2015 has taught us that Android vulnerabilities still exist. When it comes to mobile application development, protecting the privacy of users is becoming increasingly important due to the many persisting security threats.
The aim of this article is to gather together and present the security risks that we may have to confront in Android mobile application development. In fact, it’s one of the most targeted and vulnerable operating systems.
Android is precisely the most widely used operating system in the world (at least 80% of mobile devices run on it). This makes it the main target for hackers and cyber-attacks.
1. Malware or malicious software
According to the mobile security company Zimperium, 95% of Android devices are vulnerable to this kind of attack. Translated into absolute numbers this means that 900,000 devices are at risk of being hacked without their owners being aware of it.
The main access channel for these malware programmes is downloading apps outside the Google store, although this is far from being the only way they spread. There are currently just over 75,000 identified threats of this nature.
The range of malware programmes is growing on a daily basis. 79% of the time, viruses result in a higher phone bill, i.e. they increase our consumption by sending messages, spending data or making phone calls without our approval. The most common in Android according to Spanish leading telecommunications company’s blog Movisfera are:
- Andr/PJApps-C: these are apps that have been modified using a tool available on the Internet. They are not necessarily malicious but are likely to entail some kind of illegal activity.
- Andr/BBridge-A: this kind may install additional malicious apps on Android devices. It can scan a device’s SMS and delete those warning about paid-for content.
- Andr/Generic-S: these are malicious apps that range from those that involve privilege escalation exploits to aggressive adware programmes.
- Andr/BatterD-A: these apps are covertly embedded within apps that appear to be designed to save battery but whose real aim is sending personally identifiable information to a server and displaying ads on the phone.
- Andr/DrSheep-A: this malware allows hackers to hijack Facebook, Twitter or LinkedIn sessions on a wireless network environment.
2. Android fragmentation
By Android fragmentation, we mean the fact that not all mobile devices running on Google’s operating system use the same version of it. Some will have never had their OS updated, while others will be running on the most up-to-date version. Not to mention those devices that will not support new versions due to a lack of memory space.
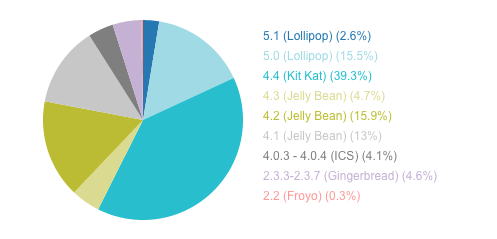
The thing is that devices that are not updated remain vulnerable due to former OS programming errors because they will not have the latest security updates. According to the distribution of Android versions in early August 2015, it is as follows:
- Lollipop 5.0 y 5.1: 18.1% of devices
- KitKat 4.4: 39.3% of devices
- JellyBean (versions 4.1 to 4.3): 33.6% of devices
- Other previous versions: 9% of devices
Source: CNet
3. Customised operating systems
Another major risk faced by Android devices which may lead to a security breach is due to the possibility of customising the operating system. This risk is faced by both phone manufacturers and mobile users.
For example, sometimes device manufacturers (such as Samsung, HTC or Huawei) modify the operating system to include their brand on Android’s OS.
On the other hand, users may also modify the operating system by incorporating customisation layers or through the so-called launchers. In these cases, Android’s OS is modified leading to security gaps as it doesn’t envisage the consequences brought about by these changes.
An example of this may be phishing programmes that change the icon settings on the device’s main screen. In this case, these shortcuts change their appearance and no longer redirect to the proper applications.
4. App downloads outside the store
We were already pointing this problem out in this article’s first section on malware. Now we would like to focus on downloading apps from sites other than the official store. Android mobile application development is simple and any developer can create a malicious application. Be careful!
Now and then users choose to download apps from unofficial sites to avoid payment. This can result in downloading a fake app or one that has been modified to install a virus on your mobile device.
5. Infiltration of malicious apps in the store
Publishing an Android app on Google Play is relatively simple. Besides, Android mobile application development is spreading like wildfire: hundreds of developers upload apps to the store every single day. And − although Google does its best to try to keep its store free from malware − it’s possible that viruses may be sneaking in.
This is precisely the reason behind Google cleaning its store from time to time: to eliminate malware or malicious applications. The aim is to remove those apps that may pose a threat to the user’s privacy and the mobile device’s security.
Google removes any published applications from the store that have been identified as containing malware. However, unfortunately, it’s always feasible that they have already been downloaded to a certain extent.
If the malicious app has been massively downloaded and many users have been affected, the solution consists in removing the infectious applications remotely. This solution is known as the kill switch.
6. Vulnerable software for mobile application development
Android’s weaknesses can be found in many places: in the operating system itself, in the apps included by default on the device, in those we download in tools coming from sources other than the platform… A striking case was Heartbleed, a breach in OpenSSL that posed a global security breach.
To sum it up, no software is completely flawless. Not even Google itself has managed to create an operating system free of security breaches. The good news is that most security breaches can be avoided if we develop apps for Android correctly and our users apply their common sense when downloading apps and granting permissions to mobile applications.